Petya Ransomware Removal And Protection

Petya Ransomware Removal And Protection Turn the computer off and disconnect from the network. petya waits about an hour after infecting a system before rebooting and displaying a message that the file system is being “repaired.”. if the machine is turned off immediately, some files may be saved, experts say. Petya ransomware encrypts your computer’s master file table (mft). the mft is your computer’s quick reference guide for every single file on your drive. without access to the mft, your computer can’t find any of its files, and so it can’t even boot up — much less function normally. after the victim unwittingly installs petya onto a.
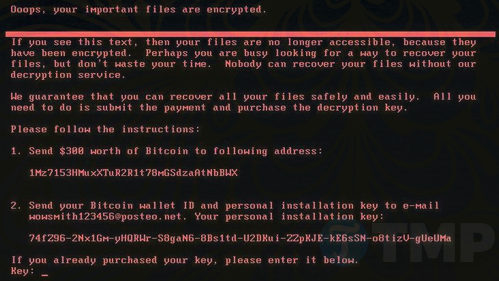
What Is Petya Ransomware How To Avoid Remove And Protect Your Computer Matt suiche, founder of comae technologies, also suggested in a medium post that petya is wiper malware disguised ransomware. "the goal of a wiper is to destroy and damage. the goal of a. Companies that run windows pcs need protection against ransomware, including petya. while many other types of ransomware need higher levels of security services, dealing with petya is pretty straightforward and the free edition of endpoint central provides that. this is a suitable package for small businesses and it will protect 25 endpoints. Notpetya was a souped up version of petya. cybersecurity experts named it “notpetya,” and the name stuck. although both petya and notpetya can help a cybercriminal launch a ransomware attack, some critical differences exist. 1. propagation. petya didn’t spread nearly as rapidly as notpetya for a few reasons. Petya can be best described as a three stage ransomware, where each stage has its own dedicated functionality: stage 0 “mbr overwrite” – overwrite the hard drive’s master boot record and implanting custom boot loader. stage 1 “mft encryption” – use the custom boot loader introduced in stage 0 to encrypt all master file table (mft.

What Is Petya Ransomware Protect Detect Notpetya was a souped up version of petya. cybersecurity experts named it “notpetya,” and the name stuck. although both petya and notpetya can help a cybercriminal launch a ransomware attack, some critical differences exist. 1. propagation. petya didn’t spread nearly as rapidly as notpetya for a few reasons. Petya can be best described as a three stage ransomware, where each stage has its own dedicated functionality: stage 0 “mbr overwrite” – overwrite the hard drive’s master boot record and implanting custom boot loader. stage 1 “mft encryption” – use the custom boot loader introduced in stage 0 to encrypt all master file table (mft. Next, make sure that your antivirus software is up to date. most antivirus companies already have patches out that block petya and this new version of it. lastly, take sensible everyday. Petya began as a run of the mill ransomware virus. it worked by encrypting both a computer’s user files as well as its hard disk. once completed, this level of encryption essentially rendered any computer inoperable. users unlucky enough to encounter it were either forced to pay $300 in bitcoin to receive a decryption key to their files or.

Understanding Petya Ransomware How To Effectively Remove And Protect Next, make sure that your antivirus software is up to date. most antivirus companies already have patches out that block petya and this new version of it. lastly, take sensible everyday. Petya began as a run of the mill ransomware virus. it worked by encrypting both a computer’s user files as well as its hard disk. once completed, this level of encryption essentially rendered any computer inoperable. users unlucky enough to encounter it were either forced to pay $300 in bitcoin to receive a decryption key to their files or.

Comments are closed.