Optimizing And Securing The Wireless 5g Iot And Beyond With Machine Learning

Machine Learning Techniques For 5g And Beyond The Iot Academy Dr. o'shea previously worked with a dod lab on software and cognitive radio applied research technologies and rapid prototyping, helping build and lead the gnu radio project, is a co chair of the ieee emerging technology area on machine learning for communications, an editor for transactions on wireless communications and tccn, co chair for. The existing literature has explored various security aspects of 5g and beyond networks in general, and more recently, the applications and potential of machine learning for 5g network security in particular. ai is envisioned to be one of the key enablers of 5g and beyond networks [6], [7]. ml algorithms are also used along with software.
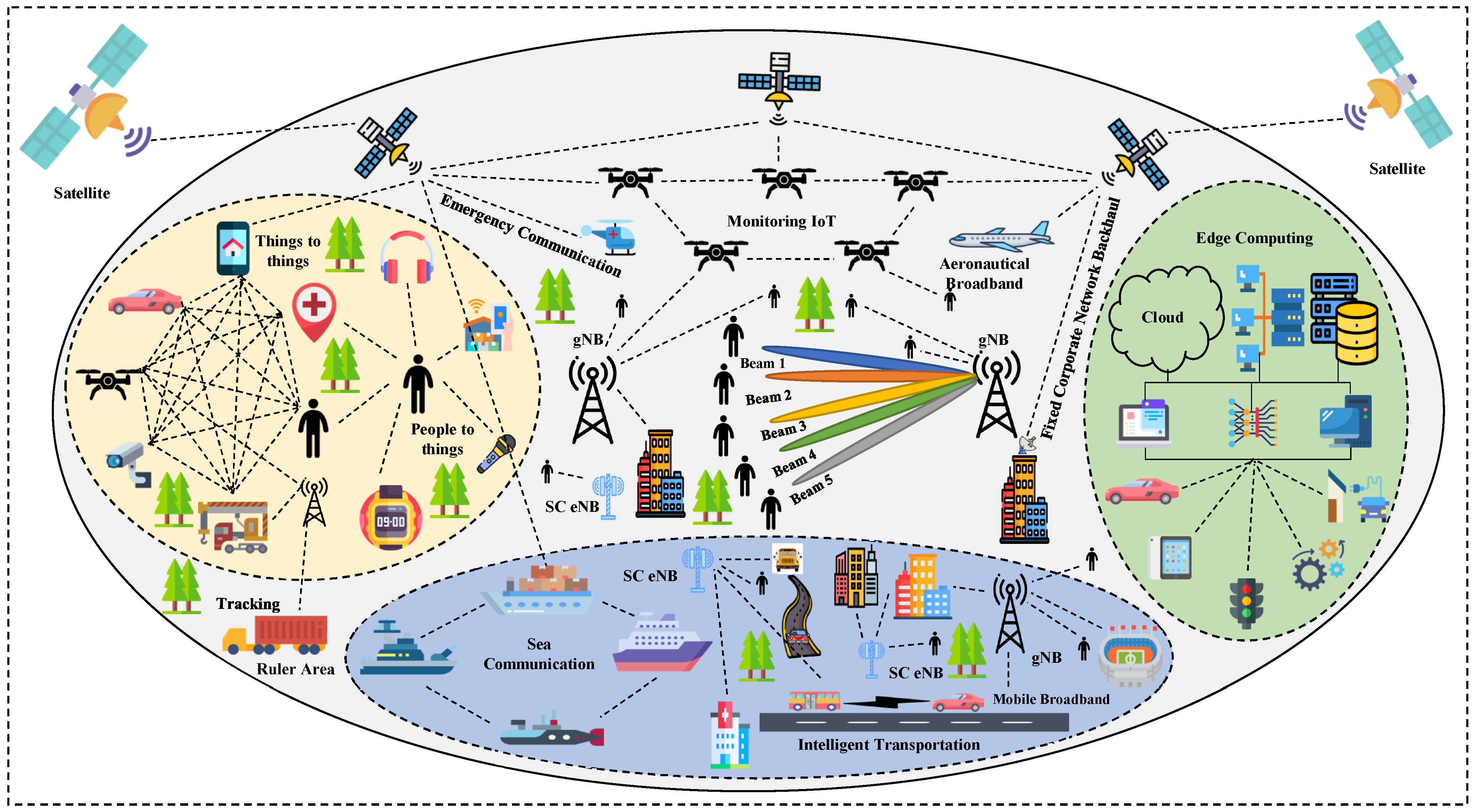
Electronics Free Full Text Machine Learning For Physical Layer In Machine learning (ml) in this context can help to provide heavily dynamic and robust security mechanisms for the software centric architecture of 5g networks. ml models’ development and implementation also rely on programmable environments; hence, they can play a vital role in designing, modelling, and automating efficient security protocols. 5g is the fifth generation of wireless communication and the future wireless technology paradigm, with the aim of ubiquitous connectivity. it envisions diverse technological solutions including uninterrupted connectivity, high bandwidth, utilization of unexplored frequency bands for wireless communication, high data capacity, low latency and superior quality of service (qos). 5g requirements. The 5g and beyond wireless networks are critical to support diverse vertical applications by connecting heterogeneous devices and machines, which directly increase vulnerability for various spoofing attacks. conventional cryptographic and physical layer authentication techniques are facing some challenges in complex dynamic wireless environments, including significant security overhead, low. The paper largely focus on deep learning techniques in iot but does not provide a solid background for the overall security architecture of iot and machine learning aspects. this makes it exhaustive only in dl. current work provides data from different domains to make it more detailed work. 2020 [24] yes: yes: no: no: no: ii, iii.

Events And Programs Commonwealth Cyber Initiative Virginia Tech The 5g and beyond wireless networks are critical to support diverse vertical applications by connecting heterogeneous devices and machines, which directly increase vulnerability for various spoofing attacks. conventional cryptographic and physical layer authentication techniques are facing some challenges in complex dynamic wireless environments, including significant security overhead, low. The paper largely focus on deep learning techniques in iot but does not provide a solid background for the overall security architecture of iot and machine learning aspects. this makes it exhaustive only in dl. current work provides data from different domains to make it more detailed work. 2020 [24] yes: yes: no: no: no: ii, iii. Fifth generation (5g) technology will play a vital role in future wireless networks. the breakthrough 5g technology will unleash a massive internet of everything (ioe), where billions of connected devices, people, and processes will be simultaneously served. the services provided by 5g include several use cases enabled by the enhanced mobile broadband, massive machine type communications, and. Machine learning for securing sdn based 5g network. the purpose of this research is to analyze the suitable machine learning (ml) for securing the sdn controller targeted by ddos attacks and proposes a security scheme that includes the ml algorithm, adaptive bandwidth mechanism, and dynamic threshold technique.

Comments are closed.