Iot Security A Multilayer Strategy To Empower The Evolution Of Iot

Iot Security A Multilayer Strategy To Empower The Evolution Of Iot Iot security — why it matters for your business. it’s estimated that by 2025, the number of iot devices will reach 30 billion. by 2030, iot could generate about $12.6 trillion in value. investments in iot capability have grown from $745 billion in 2019 to $1.1 trillion projected by the end of 2023. The internet of things (iot) is a huge, global, distributed network of interlinked heterogeneous devices armed with embedded sensors, actuators and processors enabling them to connect to the internet, exchange data, communicate and interact seamlessly with one another in real time. it enjoys wide range of applications where it holds important data, hence becoming exposed to varying degrees of.
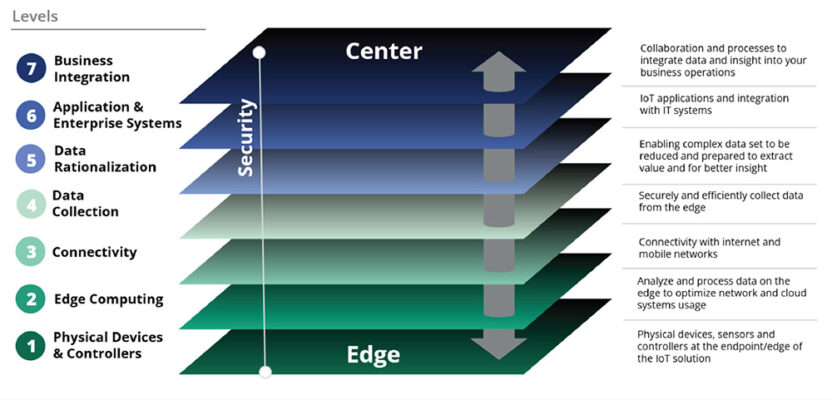
Iot Security A Multilayer Strategy To Empower The Evolution Of Iot Evolution and trends in iot security. abstract: the amount and diversity of devices that integrate connection capabilities continues to grow, and both the public and private sectors continue to explore various application areas and paradigms that involve these connected objects. yet as the iot field evolves, so too must its security capabilities. Definition of iot security. iot security is based on a cybersecurity strategy to protect iot devices and the vulnerable networks they connect to from cyber attacks. iot devices have no built in security. iot security is needed to help prevent data breaches because iot devices transfer data over the internet unencrypted and operate undetected by. Poor physical security 10. iot application security and end point security are the biggest concerns. poorly secured iot devices and applications make iot a potential target of cyberattacks. application developers or manufacturers that create iot products are not mature from a security standpoint. What is iot security? iot security refers to a strategy of safeguards that help protect these internet enabled devices from cyber attacks. it’s a fairly new discipline of cybersecurity, given the relatively recent introduction to these non standard computing devices. potential iot attacks “could range from unauthorized access and data theft.

Iot Security A Multilayer Strategy To Empower The Evolution Of Iot Poor physical security 10. iot application security and end point security are the biggest concerns. poorly secured iot devices and applications make iot a potential target of cyberattacks. application developers or manufacturers that create iot products are not mature from a security standpoint. What is iot security? iot security refers to a strategy of safeguards that help protect these internet enabled devices from cyber attacks. it’s a fairly new discipline of cybersecurity, given the relatively recent introduction to these non standard computing devices. potential iot attacks “could range from unauthorized access and data theft. The evolution of mobile technologies has introduced smarter and more connected objects into our day to day lives. this trend, known as the internet of things (iot), has applications in smart homes, smart cities, industrial automation, health monitoring systems, and has become an essential component of the communication and networking industry. Internet of things devices have become the new privileged targets for cyberattackers in recent years. this is in part due to the amount of sensitive data they provide. in parallel, security systems are becoming more and more robust with the help of machine learning (ml) algorithms. however, this advance can also benefit malicious people. in recent years, ml based smart attacks have emerged and.

Comments are closed.