Hash Functions In Blockchain Technology Training Ppt Ppt Powerpoint
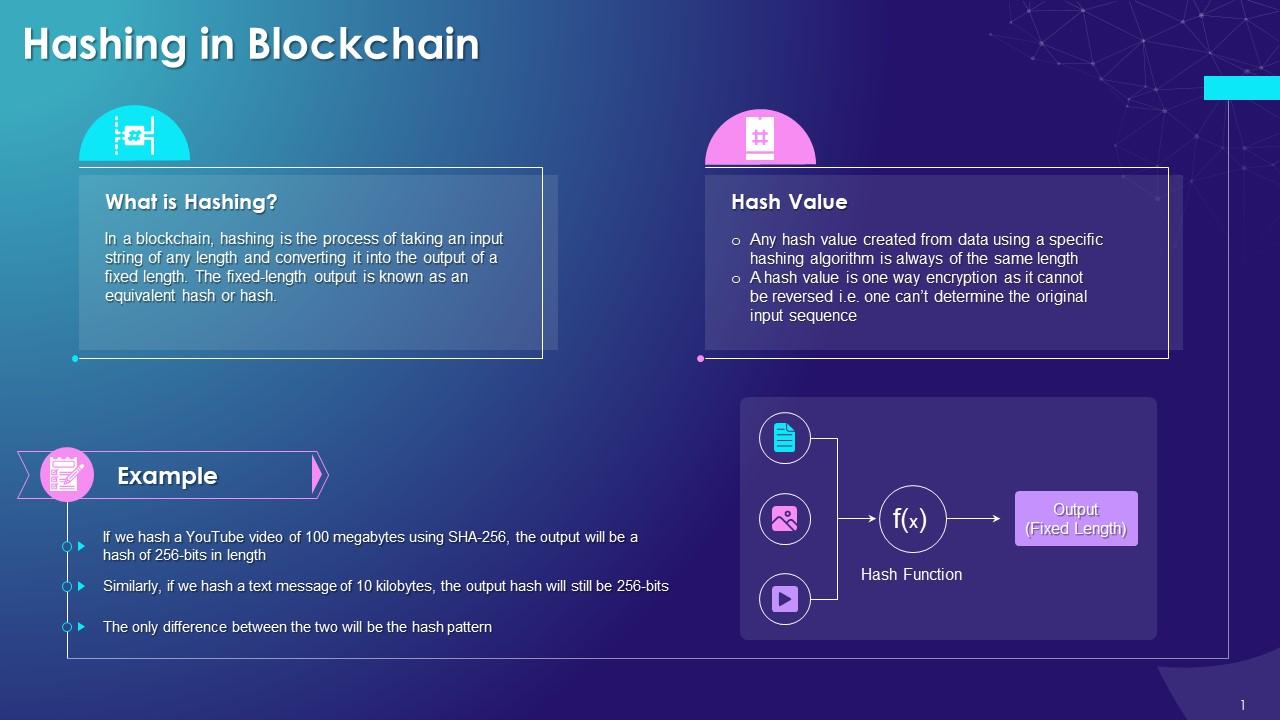
Hash Functions In Blockchain Technology Training Ppt Ppt Powerpoint The slide includes an example to highlight the avalanche concept in the blockchain. slide 5. this slide highlights the major classes of cryptographic hash functions such as secure hashing algorithm (sha 2 and sha 3), race integrity primitives evaluation message digest (ripemd), message digest algorithm 5 (md5), and blake2. instructor’s notes:. Presenting hash functions in blockchain technology. these slides are 100 percent made in powerpoint and are compatible with all screen types and monitors. they also support google slides. premium customer support is available. suitable for use by managers, employees, and organizations. these slides are easily customizable.
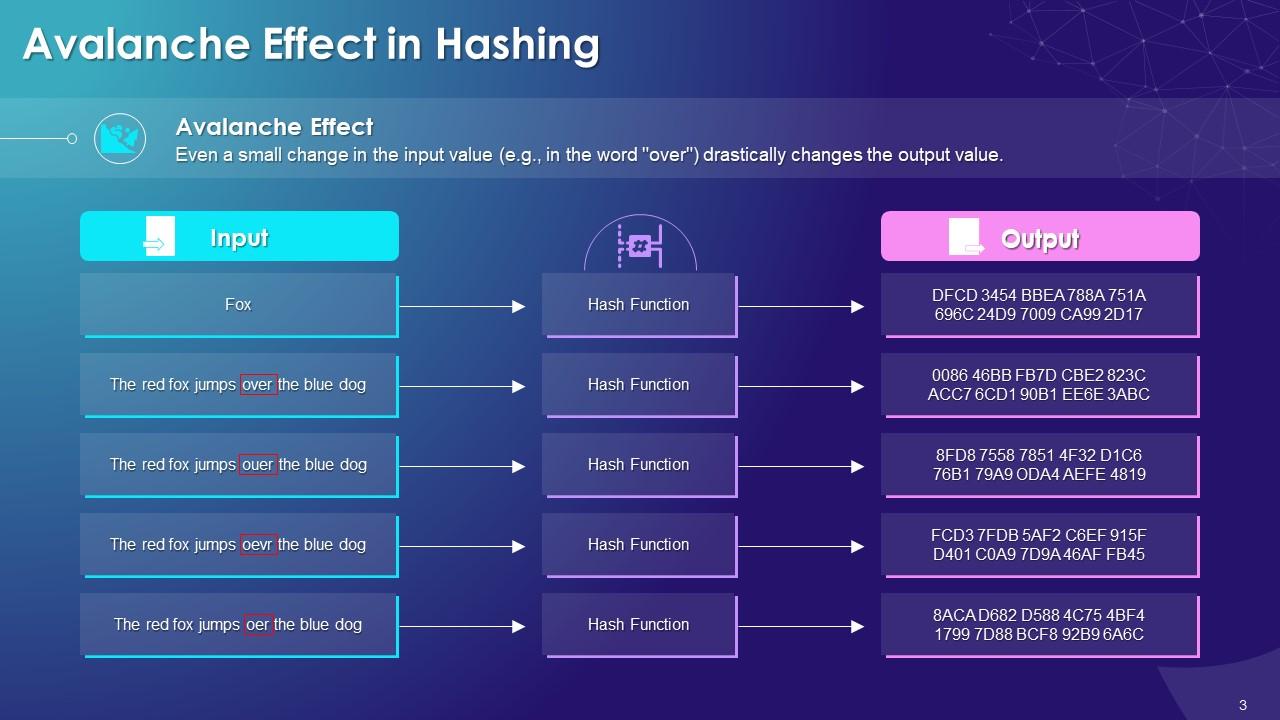
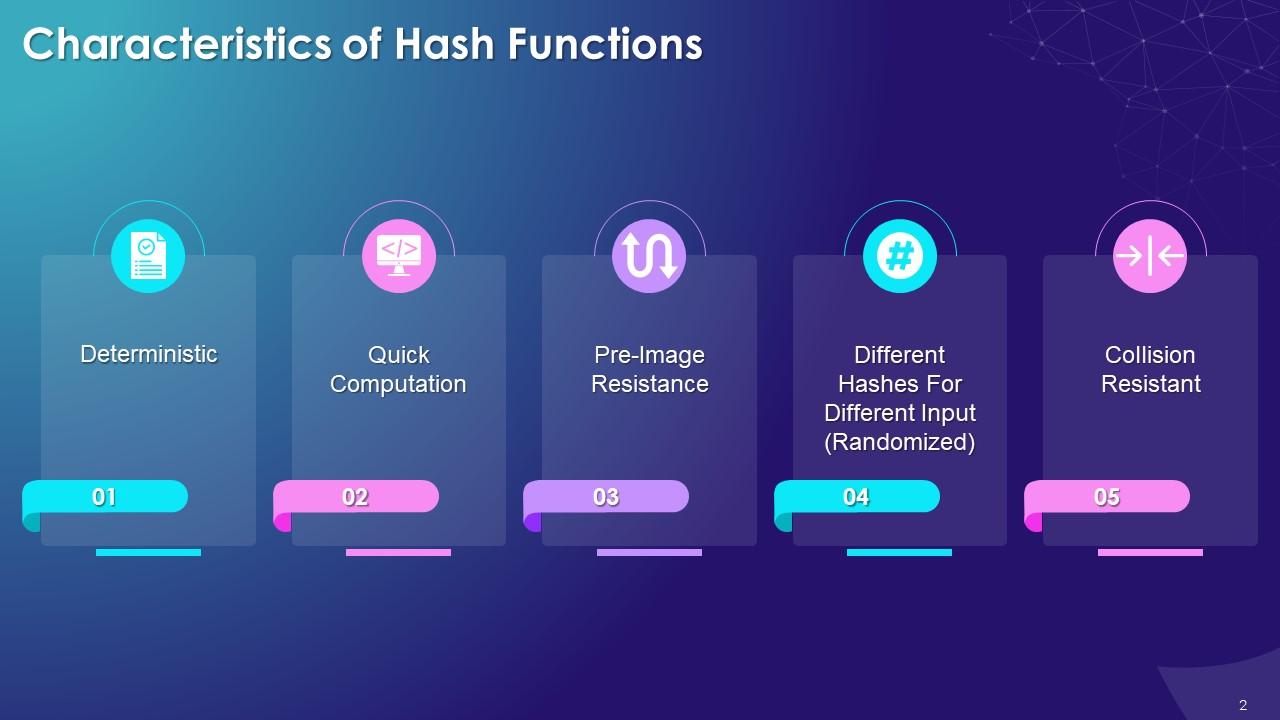
Hash Functions In Blockchain Technology Training Ppt Ppt Powerpoint The ppt module covers hashing in the blockchain and characteristics of hash functions deterministic, quick computation, pre image resistance, randomized, and collision resistant and avalanche effect. it also includes slides on types of hash functions secure hashing algorithm, race integrity primitives evaluation message digest ripemd, message. Blockchain technology powerpoint. this document provides an introduction to blockchain technology and cryptocurrency. it discusses what blockchain is, how it works using cryptography, peer to peer networks, and game theory. it also covers use cases like bitcoin, altcoins, tokens, icos, smart contracts on ethereum using solidity, and the remix. Cryptographic hash functions are an essential component empowering blockchain technology and cryptocurrencies like bitcoin. but what exactly are cryptographic hashes, and why are they so important. Hash function • the hash value represents concisely the longer message • may called the message digest • a message digest is as a ``digital fingerprint'' of the original document • condenses arbitrary message to fixed size h = h (m) chewing functions • hashing function as “chewing” or “digest” function.

Hash Functions In Blockchain Technology Training Ppt Ppt Powerpoint Cryptographic hash functions are an essential component empowering blockchain technology and cryptocurrencies like bitcoin. but what exactly are cryptographic hashes, and why are they so important. Hash function • the hash value represents concisely the longer message • may called the message digest • a message digest is as a ``digital fingerprint'' of the original document • condenses arbitrary message to fixed size h = h (m) chewing functions • hashing function as “chewing” or “digest” function. It defines blockchain as a distributed ledger of transactions stored in immutable blocks chained together using cryptography. it explains key concepts such as nodes, blocks, hashes, mining, and proof of work. blockchain allows for trustless transactions without intermediaries by achieving consensus among peers on the network. It is a stronger hash function and it still follows the design of sha 1. in 2012, the keccak algorithm was chosen as the new sha 3 standard. sha 256 is the most famous of all cryptographic hash functions because it’s used extensively in blockchain technology. the sha 256 hashing algorithm was developed by the national security agency (nsa) in.
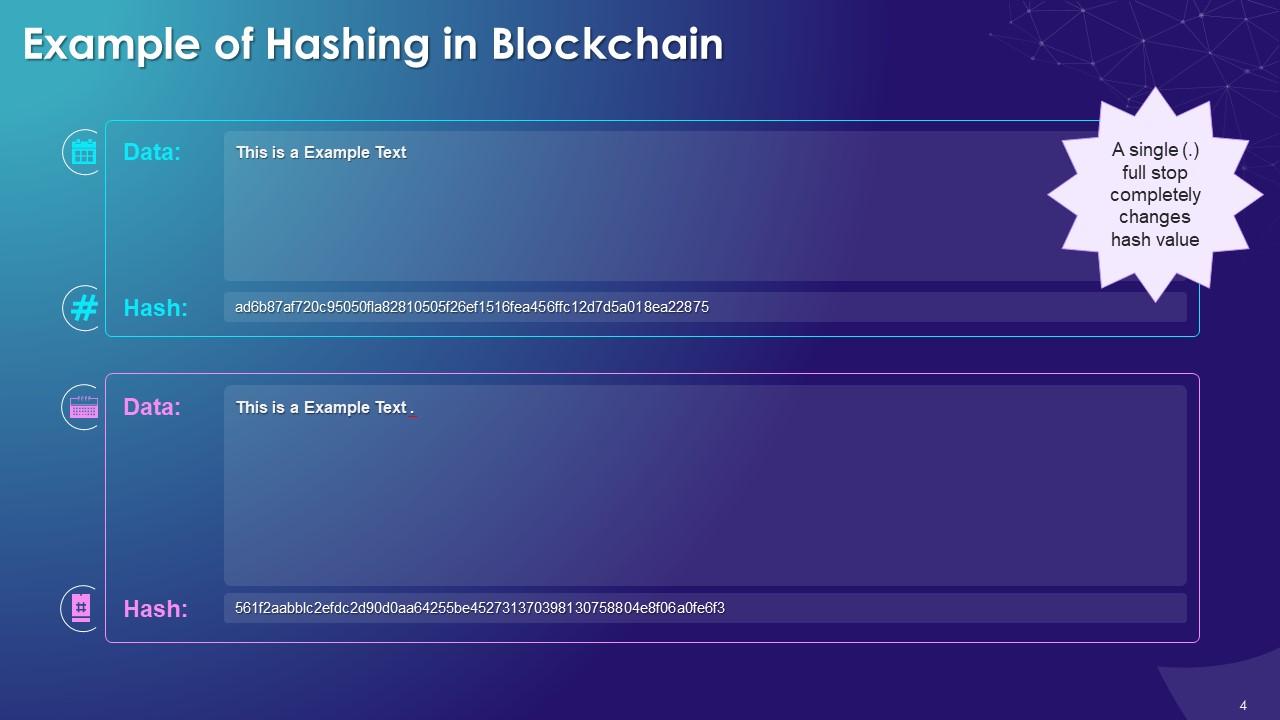
Hash Functions In Blockchain Technology Training Ppt Ppt Powerpoint It defines blockchain as a distributed ledger of transactions stored in immutable blocks chained together using cryptography. it explains key concepts such as nodes, blocks, hashes, mining, and proof of work. blockchain allows for trustless transactions without intermediaries by achieving consensus among peers on the network. It is a stronger hash function and it still follows the design of sha 1. in 2012, the keccak algorithm was chosen as the new sha 3 standard. sha 256 is the most famous of all cryptographic hash functions because it’s used extensively in blockchain technology. the sha 256 hashing algorithm was developed by the national security agency (nsa) in.
Hash Functions In Blockchain Technology Training Ppt Ppt Powerpoint

Comments are closed.