Facebook Phishing Email
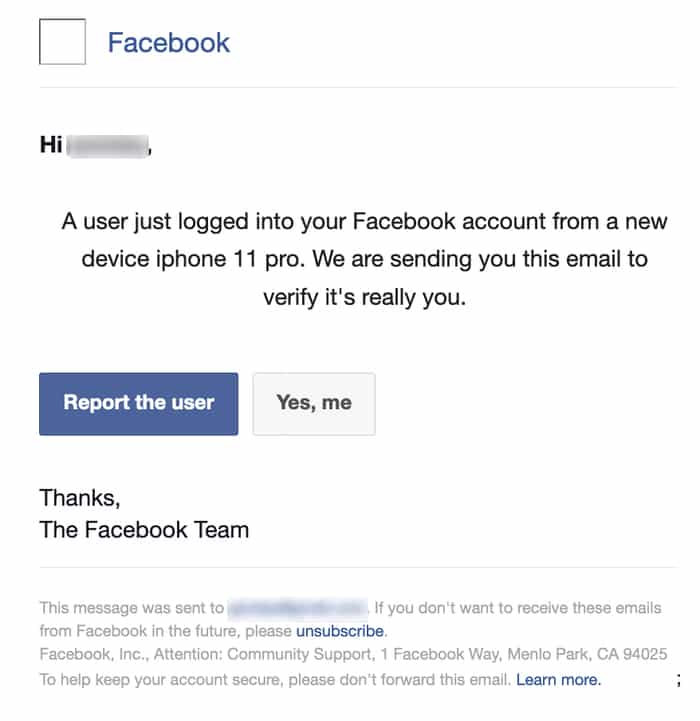
How To Protect Yourself From Facebook Phishing Emails Verified Org A "redirector" link is used to filter and verify the visitor before leading them to the final phishing page; if they do not comply with the rules, access is denied Once victims enter their The Division of Consumer Protection recommends several tips to help New Yorkers avoid falling victim to phishing scams: Do not reply to messages from unknown numbers Report the message using your
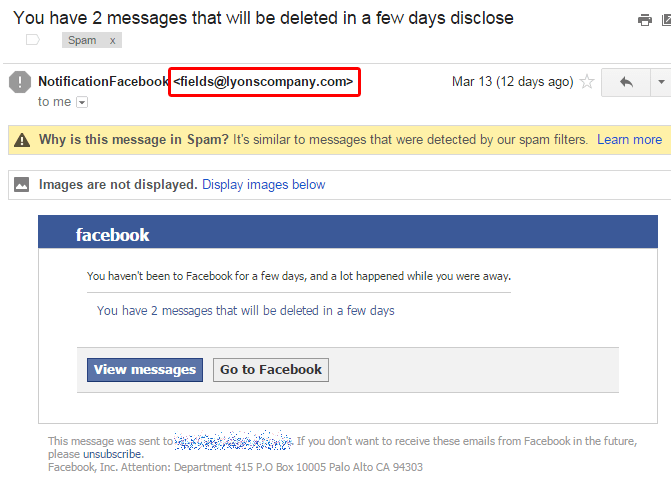
Facebook Phishing Email Charlotte-Mecklenburg Hospital Authority d/b/a Atrium Health (“Atrium Health”) posted a website notice confirming reports of GRAND JUNCTION, Colo (KJCT) - District 51 (D51) is warning staff and students of an email scam The email includes fake internship offers asking for money to “secure” a spot This is a phishing Key highlights of the research include: Lingering Vulnerability: Despite advancements in cybersecurity, 48 percent of organizations lack confidence in their existing email security defenses, leaving Using single sign-on tools to log into websites is quick and convenient, but there are several major security issues that make SSO untrustworthy

Facebook Spoofed Once Again In Multiple Variations Of A Phishing Email Scam Key highlights of the research include: Lingering Vulnerability: Despite advancements in cybersecurity, 48 percent of organizations lack confidence in their existing email security defenses, leaving Using single sign-on tools to log into websites is quick and convenient, but there are several major security issues that make SSO untrustworthy However, Microsoft strongly advises against nixing PowerShell because some core system processes and tasks may not function properly without it What’s more, doing so requires tinkering with sensitive Cyber attackers are using malicious emails to infiltrate critical national infrastructure, like utilities, transport, telecommunications, and now data centres Law enforcement has warned Apple users that hackers are using fake iCloud storage email alerts to target iPhone users as part of an information-stealing campaign An email that appears to come from AAA promises members a free emergency kit if you fill out a short survey One many explains what happened when the tried it

Comments are closed.