Cybersecurity A Quick Overview In 5 Easy Steps Tca

Cybersecurity A Quick Overview In 5 Easy Steps Tca There will be five more articles introducing the framework and giving an overview of each of the five different areas of the framework. this first article will focus on the five areas that the framework addresses – which are identify, protect, detect, respond and recover. here is a high level overview of each of these areas: 1. identify. This cybersecurity tutorial covers basic and advanced concepts, specially designed to cater to both beginners students and experienced working professionals. this cybersecurity free course helps you gain a solid introduction to the fundamentals of cybersecurity and explore a wide range of topics, including network security, cryptography, threat.
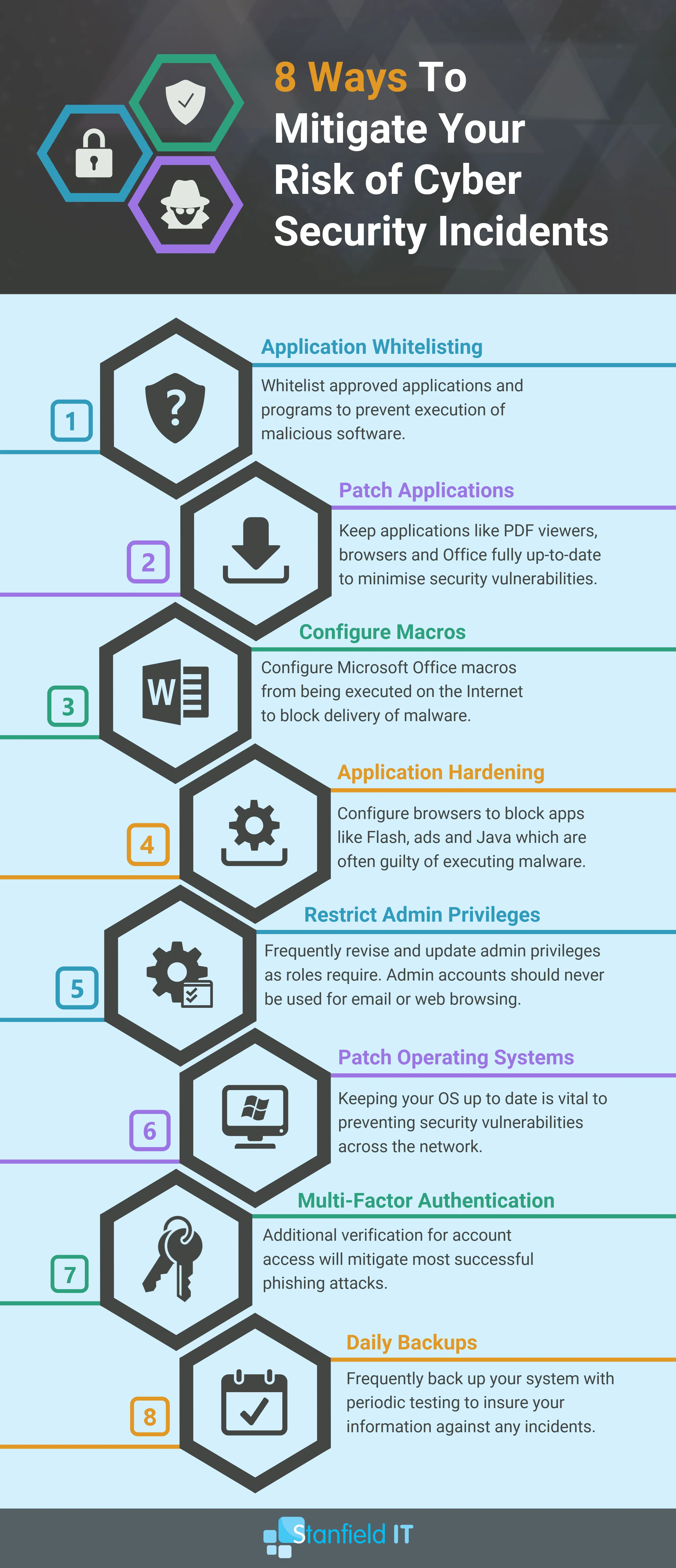
The Definitive Cyber Security Guide For Small To Medium Businesses Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given. Start with these 10 first steps. 1. adopt a risk management strategy and program plan. one of the first steps organizations can take toward an effective cybersecurity strategy and program plan is. Cybersecurity is the practice of protecting systems, networks, and programs from cyberattacks and unauthorized access. cyberattackers aim to destroy, alter, or access sensitive information for financial gain or to disrupt regular business operations. a cybersecurity strategy uses people, processes, and technology to safeguard an organization. 1. determining the scope of assessment. the first step in risk management is to determine the total scope of each assessment. while you could assess your entire organization, that is typically too big of an undertaking for one assessment. usually, it is best to start with a specific location, business unit, or business aspect.
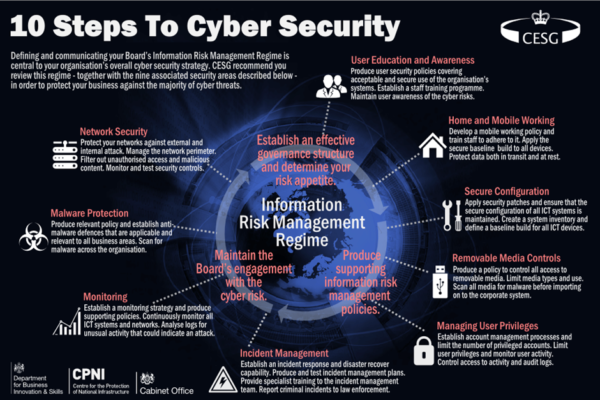
10 Steps To Cyber Security Infographic Cybersecurity is the practice of protecting systems, networks, and programs from cyberattacks and unauthorized access. cyberattackers aim to destroy, alter, or access sensitive information for financial gain or to disrupt regular business operations. a cybersecurity strategy uses people, processes, and technology to safeguard an organization. 1. determining the scope of assessment. the first step in risk management is to determine the total scope of each assessment. while you could assess your entire organization, that is typically too big of an undertaking for one assessment. usually, it is best to start with a specific location, business unit, or business aspect. Cybersecurity involves everyone and every entity — from you and your neighbors to organizations and companies to governments. it’s considered a fundamental necessity, and in this introduction to cybersecurity course, you’ll learn how to protect yourself and others from online attacks. this is a great starting point for anyone interested. Learn the cybersecurity fundamentals that will lay a foundation for securing your technology and personal life from dangerous cyber threats. includes cyber attacks, social engineering, threat actors, third party risks, intelligence sources, and more. to start this skill path, upgrade your plan. start. 16,218 learners enrolled.
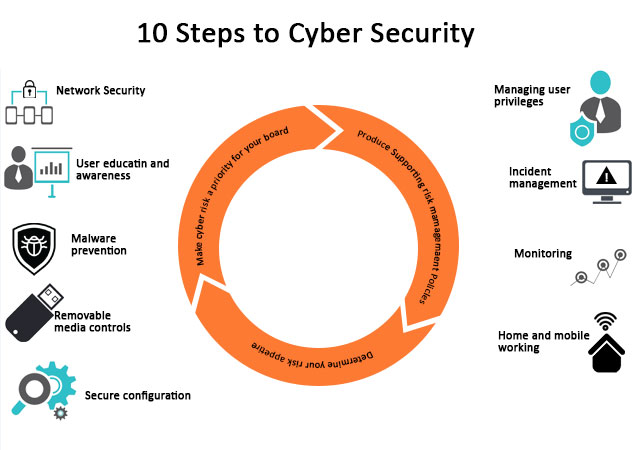
Cyber Security Principles 10 Different Principles Of Cyber Security Cybersecurity involves everyone and every entity — from you and your neighbors to organizations and companies to governments. it’s considered a fundamental necessity, and in this introduction to cybersecurity course, you’ll learn how to protect yourself and others from online attacks. this is a great starting point for anyone interested. Learn the cybersecurity fundamentals that will lay a foundation for securing your technology and personal life from dangerous cyber threats. includes cyber attacks, social engineering, threat actors, third party risks, intelligence sources, and more. to start this skill path, upgrade your plan. start. 16,218 learners enrolled.
What Is Cybersecurity A Complete Overview Guide

Comments are closed.